
Cybersecurity measures have become a requirement for businesses to secure cyber coverage. With a wide array of cybersecurity controls, organizations can be confused about which ones are most important. In the past, companies typically looked to expert opinions to determine which practices to adopt. In the report from Marsh McLennan, Using Data to Prioritize Cybersecurity Investments, analysis of proprietary data by the Marsh McLennan Cyber Risk Analytics Center shows how cyber controls compare in terms of their effectiveness. Guy Carpenter is a business of Marsh McLennan.
Marsh McLennan has a proprietary database, the Marsh Cyber Self-Assessment (CSA), composed of hundreds of questions and responses from individual organizations. When analyzed, they help describe an organization’s cybersecurity posture. The questions in the CSA focus on 12 key controls areas, along with other relevant facets of an organization’s cybersecurity posture.
12 Key Cybersecurity Controls
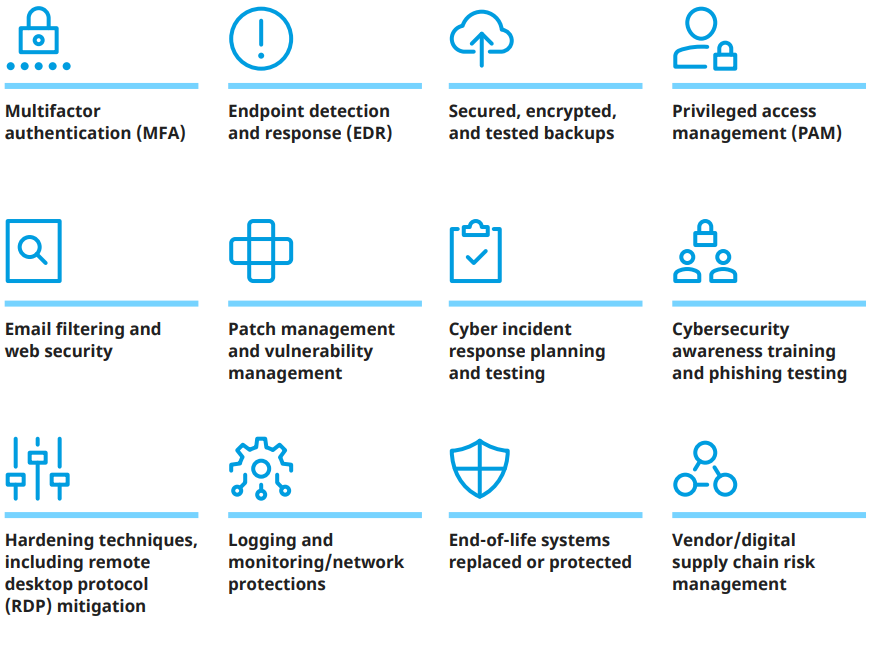
Additionally, Marsh McLennan maintains a proprietary database of historical cyber events made up of the firm’s US-based claims. When analyzed together, the two datasets provide powerful insights into which cybersecurity controls provide the greatest effect on decreasing the likelihood of an organization experiencing a cyber event.

Using Data to Prioritize Cybersecurity Investments
Previously unavailable data for analytic research can help organizations evaluate the impact of their cyber controls.